How does your organisation currently approach endpoint security?
Are there specific challenges you face in protecting your endpoints?
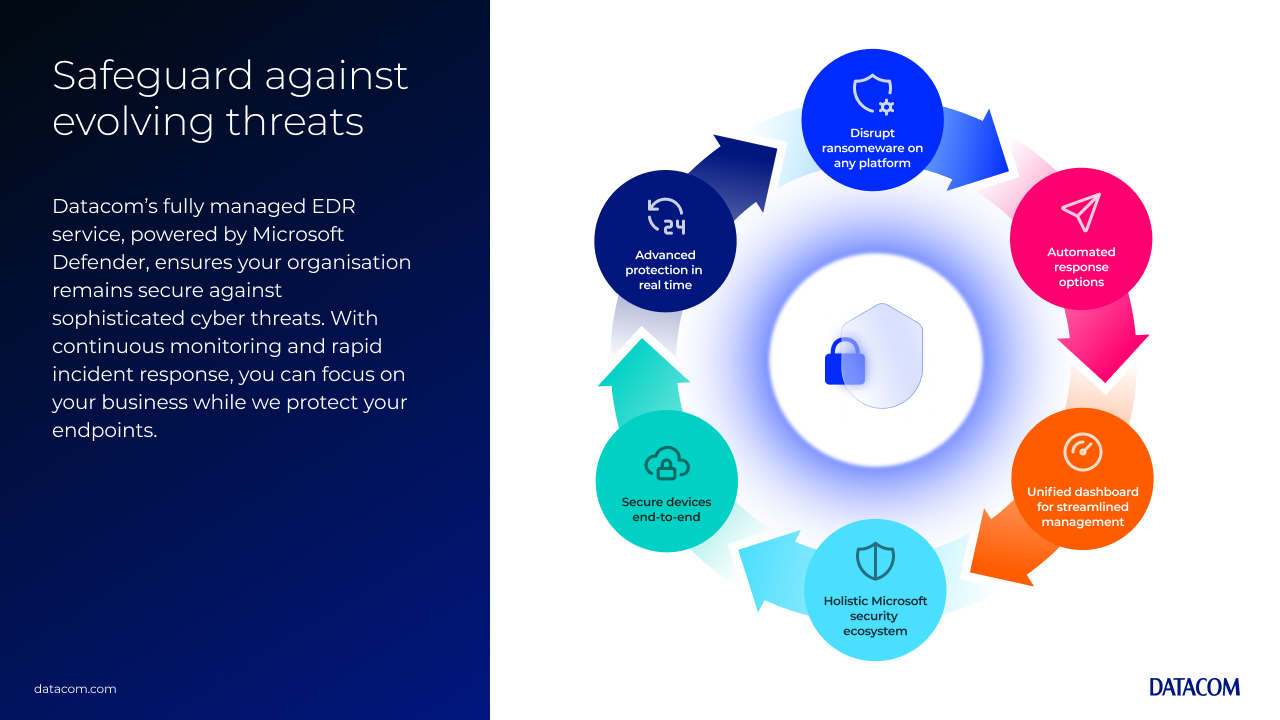
The rise of cyberattacks and the shift to remote work underscore the critical need for robust endpoint security. As organisations increasingly rely on technology, safeguarding endpoints becomes essential to protect sensitive data and maintain operational integrity.
Datacom's fully managed endpoint detection and response (EDR) service offers a tailored solution to this challenge. By integrating Microsoft’s Defender technology with the expertise of our 24/7 Cybersecurity Defence Operations Centre (CDOC), we ensure comprehensive protection for your organisation's endpoints. This service allows you to focus on what you do best, while we manage and mitigate cyber threats effectively.
Worry less with Datacom’s fully managed endpoint detection and response service.